Blog
What is GPS/GNSS Spoofing?
July 2, 2025
Will Thornton
Spoofing has been a concern in the defense space for many years, but has started to have significant impacts on civil applications around the world. But what is spoofing? Why is it happening? And how can you protect your systems?
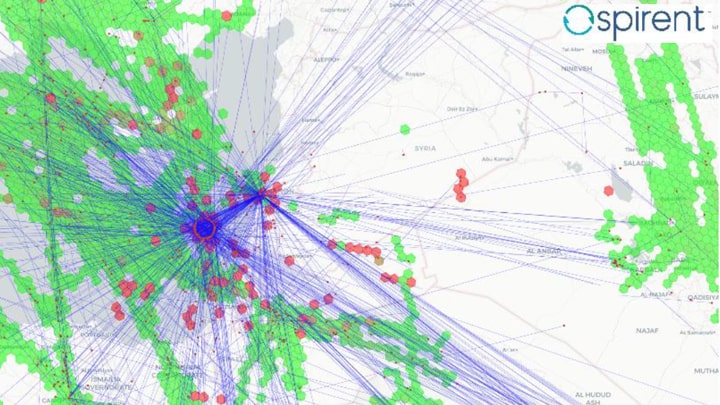
GPS/GNSS spoofing is a category of deliberate attacks on GNSS receivers. Rather than blocking signals entirely (as in jamming), spoofing aims to manipulate a receiver’s calculations, causing it to determine an incorrect position, time, or velocity without detecting a problem. In effect, spoofing tricks a system into navigating or operating based on false information.
Spoofing is a growing concern because modern society heavily depends on satellite-derived positioning, navigation, and timing (PNT). Aircraft, ships, vehicles, financial networks, power grids, and critical infrastructure increasingly rely on GNSS. Successful spoofing can cause widespread disruption, and because spoofed receivers continue functioning under false information, the danger is often invisible until significant damage occurs.
How Spoofing Works: Two Main Attack Types
Spoofing attacks generally fall into two categories:
- Radio Frequency (RF) Signal Spoofing: This is the classic form of GNSS spoofing. Attackers generate counterfeit satellite signals that mimic real GNSS signals. By controlling the timing and content of these fake signals, attackers can mislead a receiver into miscalculating its position, altitude, velocity, or time.
- Navigation Data Manipulation / Man-in-the-Middle (MITM) Attacks: In some advanced cases, spoofing can occur without generating RF signals. Attackers may interfere with GNSS processing chains—altering navigation data after it is received or compromising supporting data services. These attacks are harder to detect because they compromise trust further downstream from the RF signals themselves.
Both types of spoofing exploit the trust that navigation systems place in GNSS signals and related data streams. Successful spoofing can be subtle and highly targeted, making detection extremely challenging.
Why Spoofing Could Be Used
Spoofing attacks could be used for many reasons, ranging from criminal intent to national security operations:
- Crime: Spoofing could be used to defeat tracking systems, obscure the locations of stolen goods, or disrupt logistics and shipping operations.
- Warfare: Military forces could use spoofing to mislead enemy navigation, communications, surveillance, or weapon targeting systems.
- Terrorism: Spoofing could be used to cause confusion, accidents, or public safety crises by misdirecting aircraft, ships, or autonomous vehicles.
- Commercial Disruption: Competitors or malicious actors could use spoofing to sabotage delivery services, transport networks, or time-sensitive operations.
- Geopolitical Influence: State-sponsored actors could use spoofing to cause regional instability, disrupt trade routes, or shield sensitive installations.
As access to spoofing technologies becomes easier and cheaper, the threat landscape is expanding.
Spoofing vs. Jamming: Critical Differences
While both spoofing and jamming are forms of RF interference, they differ fundamentally:
- Jamming overwhelms GNSS signals with noise, eventually causing the receiver to lose signal lock and report a fault. GNSS jamming can degrade signals to the point where hazardously misleading information is generated – this can sometimes be confused with spoofing if the misleading information is generated without triggering a warning.
- Spoofing actively deceives the receiver with counterfeit signals, causing it to operate normally while reporting false information.
Because successful spoofing attacks often will not trigger alarms or generate obvious symptoms, and do not need power levels to be as high as a GNSS jammer, they are considered stealthier and potentially more damaging than jamming.
How to Counter GNSS Spoofing
Defending against GNSS spoofing requires a layered and adaptive approach. Some common strategies include:
- Encrypted or Authenticated Signals: Use of signals that require cryptographic authentication (such as GPS M-code or upcoming authenticated civilian signals) makes it much harder for attackers to hijack receivers. However, it should be noted that if the authentication takes place between satellite and receiver, it is likely to be ineffective against a determined MITM attack.
- Multi-Constellation, Multi-Frequency Receivers: Tracking multiple GNSS constellations (GPS, Galileo, GLONASS, BeiDou) makes a successful spoofing attack much harder to achieve.
- Advanced Signal Monitoring: Fine-tuning alarm systems to monitor for unusual behaviors—such as sudden changes in signal power levels, discrepancies between expected satellite elevation angles and observed signal strengths, or inconsistent time stamps—can improve spoofing detection.
- Advanced Antenna Technologies: Controlled Reception Pattern Antennas (CRPAs) and similar technologies allow receivers to null out or identify suspicious signal sources by analyzing signal angle of arrival, received power levels, and more. Beamforming antennas can also steer the antenna pattern to maximize gain in the direction of visible GNSS satellites, making them harder to jam and spoof.
- Integration With Other Sensors: Cross-referencing GNSS data with inertial measurement units (IMUs), terrestrial signals, alternative PNT, or other sensors can highlight inconsistencies and help systems resist or recover from spoofing attacks.
No single solution is foolproof. Building resilient navigation systems typically requires combining several of these techniques, along with regular testing and updates to keep pace with evolving spoofing tactics.
The Importance of Realistic Testing
Spoofing is no longer a hypothetical problem—it is an active, evolving threat to modern navigation and PNT systems. Understanding spoofing techniques and building resilience is critical across defense, aviation, maritime, and commercial sectors.
The only way to continuously evaluate and improve spoofing defenses is through in-field and realistic lab-based testing. Controlled spoofing simulations in a laboratory environment allow organizations to test systems safely against sophisticated attacks, refine detection capabilities, and ensure operational readiness without risking real-world disruption.
Spirent has decades of experience helping organizations test and harden systems against GNSS spoofing and other forms of RF interference. Talk to us to learn how advanced simulation can help you stay ahead in an increasingly contested navigation environment.